

Recent Posts
Microsoft’s Agentic AI Direction for Enterprise Operations
December 18th, 2025
AI in Financial Services 2025: Turning Intelligence Into Impact
December 15th, 2025
How to Build AI-Enabled Operations and Achieve Measurable Outcomes
December 10th, 2025
Prioritize Strategy to Strengthen Your Cloud Transformation
December 8th, 2025
Modern IT Service Management is Transforming Managed Services - Part 1
December 4th, 2025
Related Posts
AI Insights
Microsoft’s Agentic AI Direction for Enterprise Operations
December 18th, 2025
AI Insights
AI in Financial Services 2025: Turning Intelligence Into Impact
December 15th, 2025
AI Insights
How to Build AI-Enabled Operations and Achieve Measurable Outcomes
December 10th, 2025
Cloud Insights
Prioritize Strategy to Strengthen Your Cloud Transformation
December 8th, 2025
Cloud Insights
Modern IT Service Management is Transforming Managed Services - Part 1
December 4th, 2025
There are ways to reduce alert fatigue and prioritize threat response for effective cybersecurity that don’t distract from business objectives.
Digital transformation is underway within most organizations. This means cloud adoption is growing, trends like Bring Your Own Device are becoming more commonplace and the mobile workforce is a reality.
While all of these changes are great for agility, productivity and business velocity, they do introduce new challenges for the internal security team — one of which is alert fatigue, from the overwhelming number of security events that must be analyzed. According to the 2019 SMB Threat Landscape report, which tracked 4,000 organizations over six months, companies are facing an average of more than 3,800 security events each day.
This constant deluge of threats could easily be overwhelming, but there are ways to reduce alert fatigue and prioritize threat response for effective cybersecurity that don’t distract from business objectives.
Finding the sharpest needles in a haystack
The reality is, very few of those 3,800 daily security events will rise to the level of true security incidents. Identifying threats that matter is like trying to find the sharpest needles in the haystack — and that’s only after you’ve gotten rid of the hay. You have to consider existing security controls, the context of the systems or data at risk, and other mitigating factors to determine which threats can be ignored, which can be addressed later and which require immediate response.
No worries, though — every business has the tools and expertise to properly manage this volume of threats, right? No. Of course not. It is complex and costly to purchase and implement the right mix of cybersecurity platforms and tools, and that’s only half the battle. The real challenge is hiring and retaining cybersecurity professionals with the knowledge and skills necessary to properly configure, tune, monitor, and manage the cybersecurity infrastructure. Companies need both: the right tools to automate detection of potential suspicious or malicious activity and the right experts to find the signal in the noise and identify security events that deserve attention.
Effective threat detection
Analyzing alerts and prioritizing threats is important, but effective threat detection starts before that and includes a variety of crucial elements:
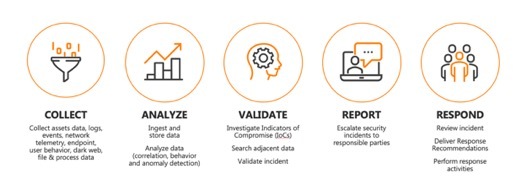 Collect: You can’t protect what you aren’t aware of. Effective cybersecurity requires an accurate inventory of the devices, applications, and data on the network, along with your organization’s current IT infrastructure, cybersecurity controls and business objectives. to make informed decisions about the potential impact of threats and properly prioritize response.
Collect: You can’t protect what you aren’t aware of. Effective cybersecurity requires an accurate inventory of the devices, applications, and data on the network, along with your organization’s current IT infrastructure, cybersecurity controls and business objectives. to make informed decisions about the potential impact of threats and properly prioritize response.
Analyze: Once a thorough accounting has been done, the next step is to assess known vulnerabilities and potential risks.
Validate: Proactive knowledge of emerging threats and impending attacks is essential. That analysis must be ongoing to enable proactive knowledge of emerging threats and impending attacks. Consistent analysis of web, log, and network data to identify suspicious activity, combined with threat intelligence related to current exploits, trends and techniques helps prepared for likely attacks.
Report: Reporting is critical, to track suspicious events that require attention. This will allow you to maintain your security posture, achieve regulatory compliance or both.
Respond: The volume and complexity of threats is more than humans alone can handle. Leverage machine learning and artificial intelligence to analyze traffic in real-time and identify patterns and suspicious activity, narrowing the focus so human cybersecurity professionals can respond only to the threats and incidents that matter.
Find a trusted partner
Cybersecurity is challenging, and it can be overwhelming to manage effectively. The good news is you don’t have to do it alone. You can reduce alert fatigue and get some peace of mind by partnering with a managed security services provider like Rackspace.
Rackspace Managed Security offers a comprehensive portfolio of security and compliance Service Blocks for all major private clouds and hyperscale public clouds, to help reduce the impact of cyberattacks on your business and help maintain compliance at a lower cost to you than acquiring in house security expertise. Rackspace Service Blocks include options for Alert Logic’s Threat Management platform, plus other best of breed industry tools, all wrapped in 24x7x365 support from Rackspace security experts.
Learn more about effective cybersecurity and reducing alert fatigue:
Tags:




